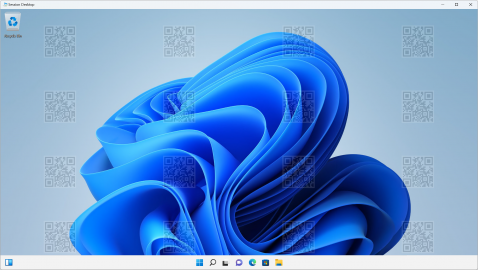
Need help learning to use the new Microsoft Azure Virtual Desktop Watermarking feature? We have it here!
Watermarking is an optional protection feature to Screen Capture in Virtual Desktop that acts as a deterrent for data leakage. This watermarking capability was first introduced in Feb 2023 via Public Preview of Windows Desktop clients. With General Availability, we’re introducing support for Azure Virtual Desktop web client.
Read how to access Watermarking support in this article.