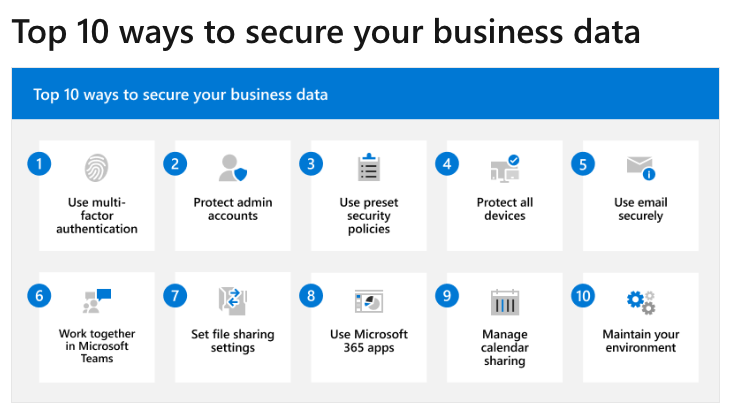
AI’s transformative power is changing the way we do business. Learn from Microsoft’s special report how AI can reshape collaborations and ignite innovation within your organization. Discover how AI can be your copilot, aiding complex tasks and boosting productivity. Explore this shift with us at A Systems Integrator, and understand how we can help you harness AI’s potential. Read the special report now to start rethinking your enterprise strategy.